I need some advice …
I have an idea for a new RedwoodJS App that would track Netlify Deploy stats. The already show Build stats, but not the stats I want – and know the numbers are there.
Originally, I was going to do Auth0 auth and have build plugins and functions “do the work” – and they still will.
But, I realized, if I need the Netlify site ids, why not use the NetlifyAPI to authorize over OAuth2, get the access token, and fetch the sites.The users signup/in will always be a Netlify user. Note: this is different from the current netlify provider, which is NetlifyIdentity.
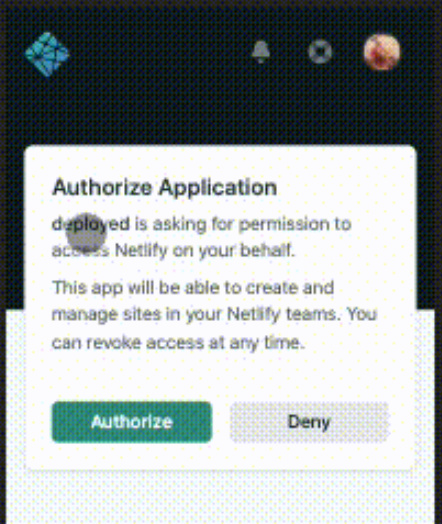
So yesterday, I implemented a first pass at NetlifyOAuth in my branch of a redwood fork:
And it works:
But, once I have an access token (my access token … your access token) I can call any NetlifyAPI endpoint on your behalf. Their api doesn’t hide any info – it’s prety much an API into their dashboard. So not only delete sites but also when pulling back a site it exposes all my private envs. I can take your db token or any other secret:
So - I cannot in all good faith do that.
My only option might be to extract only the data I need (site ids, maybe deploy ids) and trust that I don’t store your accessToken … but seems too much responsibility as a developer. And you’ll just have to trust me 
I’m going to go back to my original concept and not use the Netlify OAuth even though the experience would be nice to be able to auto setup sites and such.
It will be a better example of RW and Build Plugins and functions and that was my original intent/concept and experiment.
But, there is an example of OAuth with Netlify though I now also wonder that since it just returns a token, if I couldn’t have just extended a custom provider.
So, thoughts?